Why banking Trojans are dangerous
Virus writers are constantly developing new techniques to steal money by bypassing security systems. The most common attack vectors are those that:
- Gain unauthorized access to remote banking systems;
- Employ malware to steal confidential information;
- Steal money from accounts in online payment systems;
- Use spy Trojans to intercept data (including authentication information);
- Use encoder Trojans capable of destroying valuable files.
In many cases after a successful attack, intruders corrupt the file system on the hard disk to cover their tracks.
The most dangerous and widespread banking Trojans (number of definitions in the virus database for 2013):
- Trojan.Carberp — 13 400
- Trojan.PWS.Panda — 144 423
- Trojan.PWS.Ibank — 3 904
- Trojan.PWS.SpySweep — 14 514
- BackDoor.Termuser — 522
- Trojan.Hottrend — 2 677
- Trojan.Bayanker — 38
- Trojan.PWS.Turist — 781
Attackers often use malware for Windows in combination with Trojans for mobile platforms, especially for Android.
Below you can find brief descriptions of the most dangerous banking Trojans.
Trojan.Carberp
This malicious program steals passwords from remote banking programs and electronic trading platforms. It possesses the ability to:
- Steal passwords to access e-banking systems and trading platforms;
- Execute commands received from remote command and control (C&C) servers;
- Run a proxy server on infected computers;
- Send files found in infected systems to criminals;
- Facilitate the remote control of compromised machines;
- Render systems non-operational.
Bypass security control and monitoring software and disable anti-viruses. Infected systems can be linked into a botnet.
Trojan.PWS.Ibank
This banking Trojan can forward data, entered by users in web forms or e-banking programs, to criminals. Key functions involve the following:
- Stealing passwords entered by users and transferring them to criminals;
- Blocking access to anti-virus company websites;
- Executing commands from a C&C server;
- Running a proxy server and a VNC server on an infected computer;
- Inflicting irreparable damage to the operating system or boot sectors.
Trojan.PWS.Panda
This malicious program is also known as Zeus and Zbot. It steals passwords in infected systems. This Trojan is capable of:
- Stealing passwords stored by e-banking applications,, FTP clients and other programs;
- Executing commands received from remote C&C servers;
- Intercepting information entered by users in browser windows;
- Installing and deleting digital certificates and cookies in infected systems;
- Changing the home page in the browser;
- Blocking access to various sites;
- Downloading and launching various programs;
- Deleting files from hard drives in infected systems.
Trojan.PWS.SpySweep
This Trojan is also known as SpyEye. It is capable of the following:
- Injecting code into running processes;
- Injecting arbitrary content into web pages loaded in browser windows;
- Executing commands received from a remote C&C server;
- Intercepting information entered by users into browser windows;
- Downloading and launching various programs;
- Deleting files from the hard drive in infected systems.
BackDoor.Termuser
Trojans of this family provide criminals with access to compromised computers. This Trojan is capable of:
- Disrupting the operation of anti-virus programs and preventing them from launching.
- Executing commands from C&C servers.
- Facilitating remote control over an infected computer using RDP ("Remote Desktop") protocol, for which it creates a new account with administrator privileges.
Trojan.Hottrend
With a 20KB executable file, this is the smallest of the famous banking Trojans. It is also known as Tinba (Tiny Banker). The main purpose of this malware is to monitor Internet traffic to intercept sensitive (including banking) information and send it to criminals. This Trojan is capable of:
- Disabling system restore;
- Disrupting the operation of anti-viruses;
- Monitoring traffic, intercepting confidential information and sending it to attackers.
Trojan.Bayanker
Multi-component malware that can steal confidential information, including e-banking authorization data; rob money from accounts in electronic payment systems; and inflict damage on the file system of an infected computer. Executes commands issued by intruders.
Trojan.PWS.Turist
This Trojan is designed to steal passwords and other confidential information, especially data related to accessing e-banking systems (including those that use smart card authentication). This Trojan is capable of:
- Stealing e-banking access passwords;
- Falsifying information displayed by the e-banking client application (e.g., altering account information to conceal the fact that some money has been stolen from the account);
- Executing commands issued by intruders;
- Rendering a system non-operational.
There are banking Trojans for Android.
After the victim downloads and installs Android.SpyEye.1 on their mobile device, it starts to intercept and send all incoming SMS messages to the intruders. Android.SpyEye.1 may present danger to mobile devices owners, since it is capable of transferring confidential information into the hands of intruders.
Modern banking Trojans also carry an extensive array of features.
Example: Android.FakeSber.1.origin
A fully functional banking Trojan for Android. Designed to intercept information in SMS messages from online banking systems in Russia.
The Trojan can intercept and forward all incoming SMS messages to attackers or hide them on a compromised phone. The Trojan would be installed on the phones of users whose computers were infected with Trojan.Carberp banking malware (when attempting to use the bank's services through a web browser, users are notified by Trojan.Carberp that they need to log in from their mobile phone, and to do that, they need to install a special application onto the mobile device).
How do banking Trojans steal data?
Malware:
- Injects its code into processes that may be involved in e-banking;
- Searches for data fields in e-banking programs and stores the entered information;
- Monitors traffic for certain substrings;
- Logs keystrokes;
- Takes screenshots while the user enters sensitive information;
- Intercepts routines involved in the transmission of personal information;
- Searches for and sends digital certificates and keys to criminals.
How do banking Trojans spread?
- With spam;
- By exploiting vulnerabilities in applications;
- From compromised websites;
- With removable data-storage devices;
- With pirated software downloaded from dubious sources;
- Through the installation of other malignant programs.
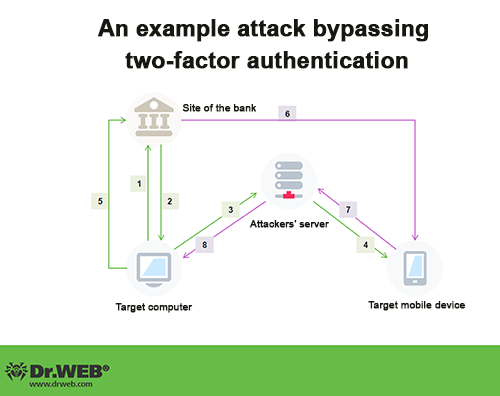
Пример реализации атаки
- A user visits a site that has been compromised.
- A vulnerability is exploited to download and install malware onto their computer.
- The Trojan connects to a remote server and sends digital certificates, and the e-banking username and password to criminals.
- When the user tries to go to the e-banking site, the Trojan displays a message in the browser window prompting the user to install onto their mobile phone the application crafted by the intruders (for example, under the guise of a security certificate).
- The victim installs the malicious application onto their smartphone.
- Attackers enter the e-banking username and password.
- The Trojan running on the mobile phone intercepts incoming short messages containing transaction confirmation codes and forwards them to the criminals.
- Attackers transfer money from the victim's account to theirs.
- To cover their tracks, they instruct the Trojan to render the system non-operational.
|
|
Booklet "The blind do not fear snakes"The main objective of Internet swindlers is to steal money. In the pursuit of their goal, they are constantly developing new versions of banking Trojans. Read this booklet yourself and recommend it to your company’s CEO and CFO. After all, protecting a company’s finances against cyber theft may guarantee the success of the organization and its employees. Go on social networks to tell your friends about this booklet and encourage them to read it! |